Blog
Gmail Alert: New Phishing Scam Poses as Google Email
Have you recently spotted an email from [email protected] in your Gmail inbox? If so, you’re not alone — and you might be at risk. A sophisticated phishing scam is making waves across the Gmail user base, cleverly designed to mimic authentic communication from Google.
Despite appearing completely legitimate, this scam is engineered to steal your login credentials and compromise your account security. Let’s break down what this phishing campaign looks like, how it works, and how to protect yourself.
What’s Happening: Phishing Disguised as Google Security Alerts
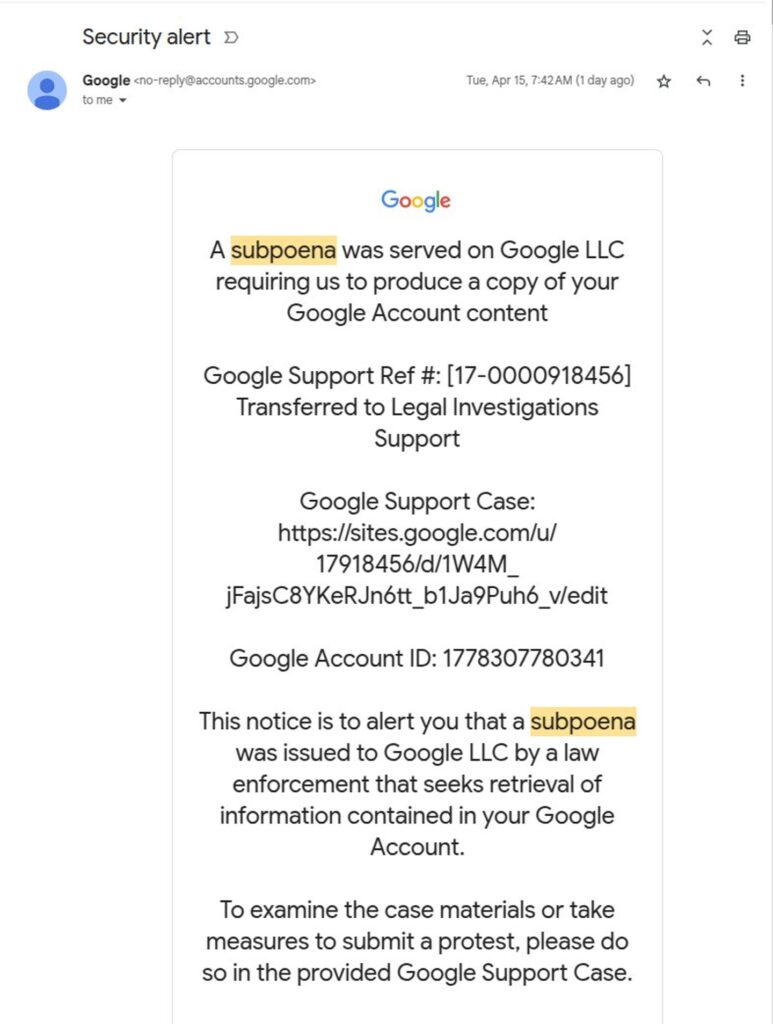
A new phishing tactic is targeting Gmail users by sending emails that appear to originate from [email protected] — a legitimate-sounding sender address typically used by Google for system notifications and security alerts.

Cybersecurity expert Nick Johnson, founder of the Ethereum Name Service, recently flagged this phishing attack as “extremely sophisticated” on social media. He even provided detailed screenshots, showing how the scam is built on top of legitimate Google infrastructure and is able to bypass standard security checks like DKIM (DomainKeys Identified Mail) validation.
How the Phishing Scam Works: A Technical Breakdown
This isn’t your average scam. Here’s a step-by-step explanation of how this phishing operation is structured:
- The Setup:
Attackers begin their operation by creating a deceptive Google account, often with a domain that appears legitimate or trustworthy at first glance, such as [email protected]. This email address is designed to mimic a professional or official source, increasing the likelihood that subsequent communications will be trusted by recipients.
Once the account is established, the scammers proceed to configure a Google OAuth application under this identity. OAuth apps are typically used by developers to request permissions to access users’ Google data, but in this scenario, the attackers manipulate the system for malicious intent.
To exploit the OAuth process, the attackers intentionally grant the app specific permissions which prompt Google’s automated systems to send a legitimate security alert to the associated email address. This alert — a standard part of Google’s security infrastructure — is generated every time a new app requests access to sensitive account data, such as Gmail or Drive.
Because the message is triggered by real activity within the Google ecosystem, it carries full authentication credentials including valid DKIM signatures and a trusted “[email protected]” sender address. The attackers then forward this email, without alteration, to their intended victim. Due to its verified origin and the presence of legitimate Google security branding, the message passes all standard email authentication checks and often lands directly in the user’s primary inbox — sometimes even within existing threads with Google.
What makes this attack particularly dangerous is how convincingly it mirrors legitimate activity. The email doesn’t contain obvious signs of phishing like suspicious links or malformed grammar. Instead, it leverages the actual infrastructure and reputation of Google to appear entirely authentic.
Victims are far more likely to engage with such a message, especially if it contains emotionally manipulative language such as claims about legal subpoenas, data breaches, or urgent security alerts. By piggybacking off Google’s automated systems, the attackers are able to bypass many traditional security filters and deliver phishing content under the guise of a trustworthy notification.
- How the Email Appears Legitimate:
One of the most deceptive aspects of this phishing campaign is that the security alert email involved is not forged — Google’s servers genuinely generate it. This gives the message a tremendous level of credibility and makes it nearly indistinguishable from legitimate notifications.
Because the email is sent through Google’s infrastructure, it effortlessly passes all standard email authenticity checks, including SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting & Conformance). These protocols are designed to verify that an email truly comes from the domain it claims to represent, and in this case, all of them validate successfully.
The email originates from [email protected], the exact address Google uses for official account communications. It includes a valid DKIM signature, which confirms that the content hasn’t been altered in transit and that Google’s servers authorized the message. This is a major reason why phishing email easily evades even the most advanced spam filters and phishing detection systems.
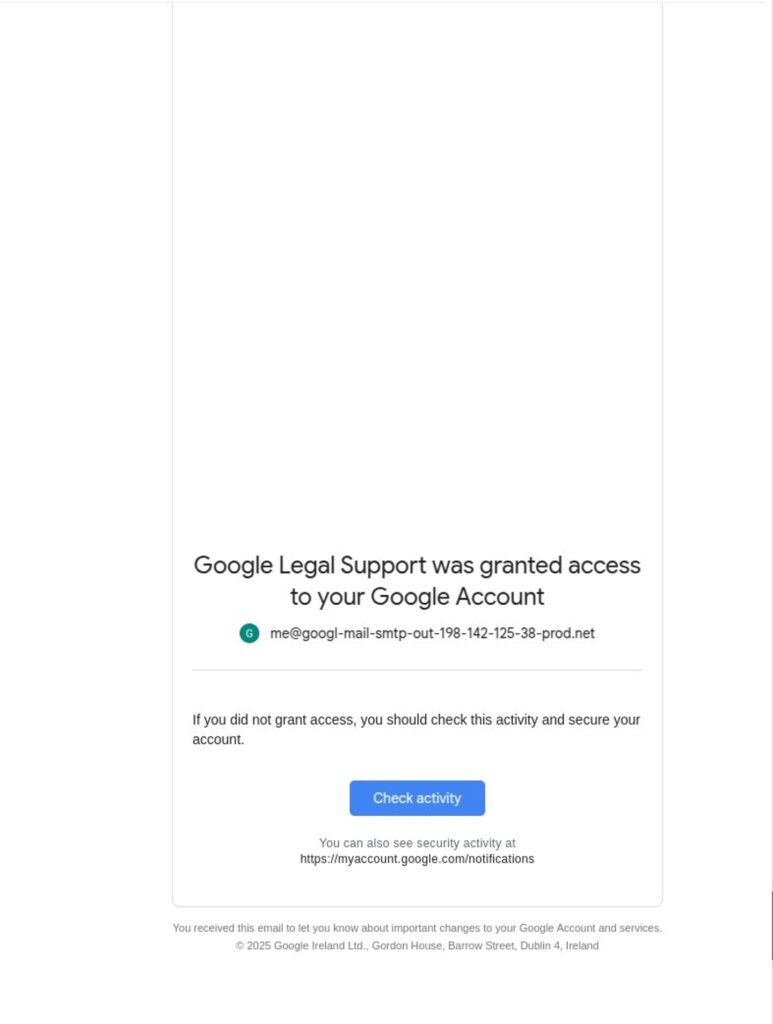
Gmail itself treats the message as a normal, trusted notification, going so far as to thread it alongside actual, prior messages from Google, such as legitimate login alerts or security updates. This seamless integration into a user’s inbox environment removes many of the visual or contextual cues that typically raise suspicion.
The result is a highly believable message that blends perfectly with legitimate correspondence, reinforcing the illusion of authenticity. Users have little reason to question the email, especially if they’ve received similar notifications in the past. It’s precisely this manipulation of trust, not through deception, but by abusing real features of the Google ecosystem, that makes this phishing tactic so insidious.
- The Scam Unfolds:
After successfully generating a legitimate-looking security alert from Google, the attacker takes the next crucial step — forwarding this email to their intended target. Because the message originates from [email protected] and is authenticated by Google’s own infrastructure, it easily bypasses spam filters and lands directly in the target’s inbox, often without any warnings or flags. The email is crafted to evoke urgency and legitimacy, often framed around a fabricated legal request, suspicious login attempt, or account verification issue.
Within the body of the email, there is a hyperlink that appears to point to a Google support page. In reality, this link directs users to a carefully crafted phishing portal hosted on Google Sites — a free service that allows users to create and publish webpages under the trusted sites.google.com domain.
The attackers exploit this by building a site that visually mimics Google’s real support or login interfaces. This isn’t just a basic mockup; the design, fonts, layout, and even language are fine-tuned to replicate Google’s official aesthetic, making it incredibly difficult for the average user to recognize the difference.
Once on this fake support page, users are presented with options like “Upload additional documents” or “View case”, actions that are designed to appear procedural and routine. These calls-to-action are engineered to push users further into the phishing funnel. When clicked, these buttons redirect to yet another spoofed page — this time, a nearly pixel-perfect clone of the Google sign-in screen.
Here lies the final trap: when a user inputs their email and password into this fraudulent login form, their credentials are instantly captured by the attackers. Unlike traditional phishing schemes that use generic or foreign-looking URLs, this attack benefits from the credibility of Google’s own domain infrastructure — especially since sites.google.com is trusted by many email clients and security tools by default.
Once the attackers have the login details, they can gain full access to the victim’s Google account, including Gmail, Drive, Photos, and any other services tied to that email. This level of access opens the door to identity theft, data harvesting, financial fraud, or even compromising additional accounts linked to the primary email address.
Why This Scam Is Dangerous
There are several reasons this phishing attack is particularly dangerous:
- Legitimacy: Because Google servers actually send the initial email, it’s nearly impossible to detect using traditional spam or phishing filters.
- Signed and Verified: The email is fully DKIM-signed, which adds another layer of perceived authenticity.
- Thread Injection: Gmail adds the message into the same thread as prior Google alerts, making it feel even more genuine.
- Convincing Portal: The phishing site is hosted on a google.com subdomain, tricking users who aren’t watching closely.
Clues to Spot the Scam
Despite how polished this scam is, there are subtle red flags you can look for:
1. Look at the Sending Domain
- While the email address may appear as [email protected], the actual sending domain in the header might be different — such as privateemail.com.
- Always inspect the email headers to verify the sender’s identity.
2. Suspicious Use of Google Sites
- Google allows users to create their own content on sites.google.com. Scammers exploit this by crafting support pages that mimic real Google portals.
- If a support or login page is hosted on sites.google.com rather than accounts.google.com, it’s likely a scam.
3. Unusual Formatting and White Space
- Johnson pointed out that these phishing emails often include a large section of white space to bury suspicious elements or make the layout feel more legitimate.
- Any email with odd spacing or formatting inconsistencies should be scrutinized.
4. ‘me@’ Address Deception
- Google displays “me” at the top of emails addressed to your own account. Attackers name their Google account as “me@…” so that Gmail makes it look like the message was sent directly to you.
Google’s Response and Recommendations
In response to this phishing method, a Google spokesperson acknowledged the attack and stated:
“We’re aware of this class of targeted attack from this threat actor and have rolled out protections to shut down this avenue for abuse. In the meantime, we encourage users to adopt two-factor authentication and passkeys, which provide strong protection against these kinds of phishing campaigns.”
They also confirmed that the OAuth-related loophole exploited in this attack is being addressed.
How to Protect Yourself From Gmail Phishing Attacks
If you’re a Gmail user — whether for personal use or business — here are some steps you can take to stay protected:
1. Enable Two-Factor Authentication (2FA)
- Always use 2FA or passkeys for your Google account. This prevents attackers from logging in even if they get your password.
2. Check URLs Carefully
- Before clicking any link in an email, hover over it to preview the full URL.
- Make sure sign-in pages start with https://accounts.google.com.
3. Review OAuth App Permissions
- Visit Google’s Security Checkup to see which apps and devices have access to your account.
- Revoke access for any unfamiliar applications.
4. Use a Password Manager
- Password managers often recognize real login pages and can flag or refuse to auto-fill on fake ones.
5. Report Suspicious Emails
- If you suspect an email is phishing, click the three dots in Gmail next to the reply button and select “Report phishing.”
Why This Attack Matters More Than Ever
This incident highlights a growing trend: phishing scams are no longer riddled with spelling mistakes and obvious red flags. Today’s attackers are using official channels, real servers, and sophisticated tricks to bypass filters and fool users.
What makes this case particularly important is the fact that the email was sent by Google, yet used against Gmail users. It shows how critical it is for tech companies to continuously evaluate their infrastructure for potential abuse — even from within their own systems.
Final Thoughts
The ‘[email protected]’ phishing scam is a sobering reminder of how clever today’s attackers can be. Even tech-savvy users might struggle to spot the deception without careful inspection.
While Google is actively working to patch the vulnerabilities exploited in this scam, users should remain cautious. Keep your guard up, enable additional security layers like 2FA or passkeys, and always verify links before clicking.
If you’ve already interacted with a suspicious email like this, immediately change your password, revoke any unauthorized app access, and consider running a full security checkup on your Google account. Stay alert — the inbox is no longer a safe space by default.
FAQs
It’s a phishing email that looks like a real Google alert but leads to fake pages stealing your login details.
Check the link URLs—if it’s on sites.google.com instead of accounts.google.com, it’s likely fake.
Because the phishing email is actually generated by Google’s servers via OAuth, it passes all email checks.
Yes, attackers trigger real Google alerts, so the email truly comes from that official address.
Change your password immediately, enable 2FA, and review your account activity for suspicious access.
Google Sites is safe but abused because scammers can host fake pages under trusted Google domains.
In Gmail, click the three dots on the email and select “Report phishing” to notify Google.
DKIM verifies emails; scammers don’t bypass it but exploit Google’s OAuth to send legitimate signed emails.
Use two-factor authentication and only enter your credentials on official Google sign-in pages.
Yes, the scam is still active, and users should stay alert and follow Google’s security advice.
-

 Blog4 years ago
Blog4 years ago10 Celebrities and Their Equally Gorgeous Siblings
-

 Blog4 years ago
Blog4 years agoThe highest-paid actors of all time are living large
-

 Blog4 years ago
Blog4 years agoHollywood Stars’ Instagram Photos viciously replayed
-

 Blog4 years ago
Blog4 years agoUpsetting And Creepy Facts We Wish We Could Erase From Our Memory
-

 Blog4 years ago
Blog4 years agoBecome Star Quality With These Celebrity Morning Routines
-

 Blog4 years ago
Blog4 years agoSome of Hollywood’s best-known movies have secrets that will shock you
-

 Blog4 years ago
Blog4 years agoThese Celebrity Couples Did Some Bizaree Things In The Name Of Love
-

 Blog4 years ago
Blog4 years agoUsing Everyday Items These People Made The Most Amazing DIY Creations